Air-Gapped System and Security Explained
When it comes to securing high-value data – state secrets, black ops logistics, nuclear launch codes, or your personal fortune in crypto keys – the best defense isn’t a firewall. It’s complete isolation.
What’s an Air-Gapped System?
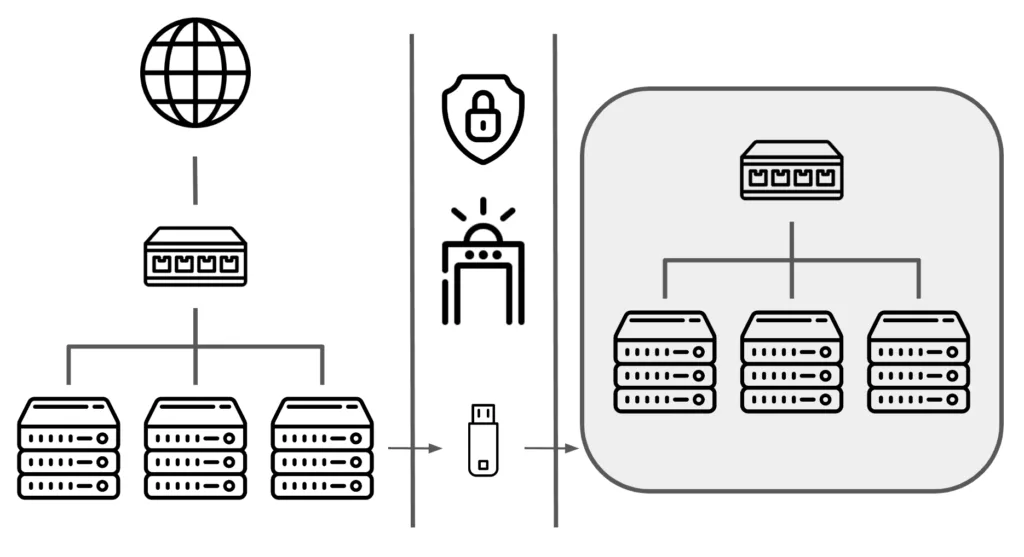
An air-gapped system is a computer, device, or network that’s physically isolated from unsecured networks like the public internet or even internal intranets. No cables. No Wi-Fi. No Bluetooth. Nada. Think of it like a safe room with no doors or windows, only way in or out is if someone physically walks in carrying something.
These setups are used in highly sensitive environments – military command centers, intelligence agencies, critical infrastructure facilities, and even by private sector firms handling proprietary data or high-stakes financials. But can also be something as simple as your own mobile phone or tablet.
• No Network Connections: It can’t connect to the internet, cloud services, or even other computers on a local network.
• Physical Data Transfers Only: Files must be moved using physical media like USB drives, CDs, or external hard drives.
• Used For High-Security Environments: Think intelligence agencies, military systems, and critical infrastructure like power grids or financial vaults.
This kind of setup doesn’t rely on software firewalls or encryption as the first line of defense, it relies on physical isolation. That’s the strength. If no one’s connected, no one’s sneaking in through the wire.
In Layman’s Terms
In basic terms, it’s like keeping your most valuable secrets locked in a safe that’s not only off the grid, but hidden in a room with no doors, no windows, and no phone lines. It means the computer or system isn’t connected to the internet or any other network, so hackers can’t get to it remotely. If anyone wants access, they have to physically walk in and plug something into it – no online shortcuts, no remote break-ins. It’s old-school, but when done right, it’s one of the toughest setups to crack.
Why Go That Extreme?
Because nothing connected is ever truly secure. You could have next-gen encryption, behavior-based threat detection, and AI-driven firewalls, but if there’s a connection, there’s a way in. An air gap shuts that down cold. No signal, no attack vector – at least not through conventional means.
It’s the purest form of passive defense. That’s solid tradecraft when you’re guarding data that could cost lives if it leaks.
The whole point is control. When you’re dealing with critical systems (like nuclear command infrastructure or covert operation logs) you can’t afford to leave any doors, even digital ones, cracked open. The internet’s a warzone, and every connection is a potential breach point. Nation-state actors, cyber mercenaries, even rogue insiders, someone’s always probing for a weakness.
With an air-gapped setup, you’re stripping them of their most powerful weapon: remote access. You’re forcing any adversary to show up in person, take risks, and leave a trail. That shift from digital to physical turns a silent, anonymous cyberattack into a high-stakes operation, and most threat actors aren’t ready to play at that level.
But Wait, Is It 100% Secure?
Short answer? No. Nothing is.
If someone wants in bad enough, they’ll try every angle – compromised USB drives, insider threats, electromagnetic leaks (look up TEMPEST attacks), or even using air-gap jumping malware like Stuxnet. Yeah, that’s the one that wrecked Iranian centrifuges using an infected USB drive. That was high-level tradecraft in action.
• USB-Based Attacks: An infected USB drive is still the most common way to breach an air-gapped system. Plug it in, and the malware does the rest – silent, fast, and devastating.
• Insider Threats: An air gap is only as strong as the people guarding it. A rogue employee or a well-compromised asset can walk critical data out or walk malicious code in.
• Electromagnetic Side-Channel Attacks: Even with no connection, some attackers can intercept signals from screens, keyboards, or power fluctuations. That’s deep surveillance-level stuff, but it’s real.
So while air-gapped systems drastically reduce attack surface, they also shift the battlefield to physical access and social engineering. That means operatives and internal security have to be airtight, too. It’s not a magic shield, but more like a bunker – you’re a lot harder to hit, but if someone makes it inside, the damage can still be lethal. That’s why real security demands airtight tradecraft across the board.
Air-Gapping For Personal Use
While air-gapped systems are mostly used by governments, militaries, and corporations handling classified intel, there’s nothing stopping individuals from using the same strategy to protect their most sensitive data. Whether you’re a journalist with confidential sources, a whistleblower, a privacy-focused individual, or just someone who doesn’t trust cloud storage, creating your own air-gapped setup is entirely possible – just takes a little discipline and know-how.
• Use an old laptop or PC that’s completely wiped and never connected to Wi-Fi, Bluetooth, or Ethernet.
• Disable all wireless components from BIOS/UEFI and keep the system physically isolated from networked devices.
• Only transfer files using brand-new, trusted USB drives that have been scanned on a secure, clean machine.
• Install a reliable operating system like Linux or a hardened version of Windows, and keep it minimal – no bloat, no extra services.
• Store critical documents, crypto wallets, or encryption keys offline and only power on the machine when absolutely necessary.
Air-gapping for personal use won’t be as seamless as storing stuff in the cloud, but that’s the point. It forces you to slow down and think like an operative; every action deliberate, every connection controlled. It’s not for everyone, but if your data’s worth protecting, this level of security puts the power back in your hands.
Operational Challenges
Air-gapped systems don’t play nice with convenience. Transferring files requires sneakernet – physically moving data via USBs or other media. That slows everything down and introduces human risk every time someone plugs something in. You’ve gotta trust your people, their processes, and run serious counter-surveillance on supply chains and personnel.
And yeah, updates are a pain. Patching systems without network access? Manual. Tedious. And often delayed. That’s a vulnerability in itself if your team’s not disciplined.
Another big hurdle is monitoring. Since the system isn’t connected, you can’t use traditional real-time monitoring tools or remote logging. Everything has to be pulled manually or through tightly controlled, periodic processes. That means spotting breaches or anomalies takes longer, and response time can lag.
You’re trading speed for security, and if your operation needs both, you’ll have to build clever workarounds without blowing the air gap. That’s where real tradecraft earns its paycheck.
So, Is It Worth It?
If your data’s that valuable – yes. Absolutely.
Air gaps are still one of the most effective ways to secure crown jewel assets, assuming the rest of your tradecraft is tight. But like any good operation, it’s about layers. Combine air-gapping with physical security, vetted personnel, encrypted storage, and rigorous monitoring, and you’ve got a serious defensive posture.
An air-gapped system isn’t about keeping up with the tech arms race. It’s about stepping off the battlefield entirely. It says, “You want in? Come and get it, but you’ll have to do it the hard way.” And in this line of work, the hard way is exactly where you want your adversaries to be.
[INTEL : Conducting Your Own Cybersecurity Audits]